Defenders can use BloodHound to identify and eliminate those same attack paths. I work for a data management company as a solutions engineer focusing on hardware but just accepted an offer to transfer to a cloud solutions architect role for the microsoft azure platform.

The Case Of The Sysinternals Blocking Malware Malware Malware Removal Microsof
BloodHound also supports Azure.

Bloodhound azure ad. This is a fork of the BloodHound UI containing Azure AD features. Users typically green with a person Computers red with a screen Groups yellow with a few people and Domains green-blue with a globe like icon. In this article you will learn how to identify common AD security issues by using BloodHound to sniff them out.
This release is authored by myself Andy Robbins Rohan Vazarkar and Ryan Hausknecht with special thanks to Will Schroeder and Lee Christensen. Return All Azure Users that are part of the Global Administrator Role. Defenders can use BloodHound.
Were excited to expand BloodHound outside the scope of on-prem Active Directory and eager to hear your experiences with using BloodHound to analyze attack paths that include Azure. To check your PowerShell version use PSVersionTablePSVersion. The enumeration allows a graph of domain devices users actively signed into devices and resources along with all their permissions.
BloodHound is an application developed with one purpose. BloodHound uses graph theory to reveal the hidden and often unintended relationships within an Active Directory environment. BloodHound with Azure AD capabilities.
This means that things work but that you may have to write your own Cypher queries to see the results you need and that clicking on Azure AD specific node types wont always work or show useful results. I was looking at certs in the Azure space and Ive narrowed it down to either the AZ-104 Admin or the 2 part Azure solutions architect expert 303304. Both blue and red teams can use BloodHound.
AzureHound uses the Az Azure PowerShell module and Azure AD PowerShell module for gathering data within Azure and Azure AD. Microsoft MVP Microsoft Azure AD AzureAD Microsofts Azure Active Directory account tweets info about Azure AD topics. Attackers can use BloodHound to easily identify highly complex attack paths that would otherwise be impossible to quickly identify.
BloodHound is a single page Javascript web application built on top of Linkurious compiled with Electron with a Neo4j database fed by a C data collector. Im sure there are a bunch I forgot. Azure Active Directory Azure AD is Microsofts cloud-based identity and access management service Azure AD Classification.
Tenants Azure Users Azure Security Groups Apps. Will Harmj0y wrote PowerView the original Bloodhound ingest PowerShell script Rubeus and more. Dont follow NerdPyle since he doesnt talk AD anymore.
Attackers can use the visual information. The Blue Team can use BloodHound to identify and fix those same attack patterns. Attackers can discover and abuse weak permission configurations for.
BloodHound uses graph theory to reveal the hidden and often unintended relationships within an Active Directory environment. If the modules are not installed you can use the -Install switch to install them. Um die Daten aus der Azure-Infrastruktur extrahieren und abbilden zu knnen erhlt der BloodHound-Graph zehn neue Knoten.
Now I am very proud to announce the release of BloodHound 40. For defenders we hope the BloodHound GUI offers an easier and more effective auditing capability to fully understand which and how many principals have control of any given object or can gain control. As of version 40 BloodHound now also supports Azure.
Since then BloodHound has been used by attackers and defenders alike to identify and analyze attack paths in on-prem Active Directory environments. In the graph world where BloodHound operates a Node is an active directory AD object. It does so by using graph theory to find the shortest path for an attacker to traverse to elevate their privileges within the domain.
The different notes in BloodHound are represented using different icons and colours. The modules require PowerShell version 51 and greater. This project is part of ROADtools and currently in alpha stage.
BloodHound is a popular open-source tool for enumerating and visualizing the domain Active Directory and is used by red teams and attackers as a post-exploitation tool. Ive picked up the AZ-900 already so im looking for the next step. Return All On-Prem users with edges to Azure.
There are also others such as organizational units OUs and. BloodHound is programmed to generate graphs that reveal the hidden and relationships within an Active Directory Network. Active Directory lokal oder in der Cloud angreifen Insbesondere bei hybriden Infrastrukturen klassisches Active Directory und Azure AD im parallelen Einsatz oder fr VMs bei Azure ist es sinnvoll die Daten aus beiden Verzeichnisdiensten in eine Datenbank und damit in einen Graphen zu laden.
Download the Custom Queries json file here. BloodHound is a free tool that uses graph theory to search out relationships in AD domains and expose the easiest way for attackers to elevate privileges. Die Software kann auf diese Weise eventuell zustzliche Angriffspfade abbilden die zuvor.
MATCH p n-rAZGlobalAdmin1-m RETURN p. BloodHound enables the Attackers to identify complex attack paths that would otherwise be not possible to identify. Attackers can use BloodHound to easily identify highly complex attack paths that would otherwise be impossible to quickly identify.
To find relationships within an Active Directory AD domain to discover attack paths.
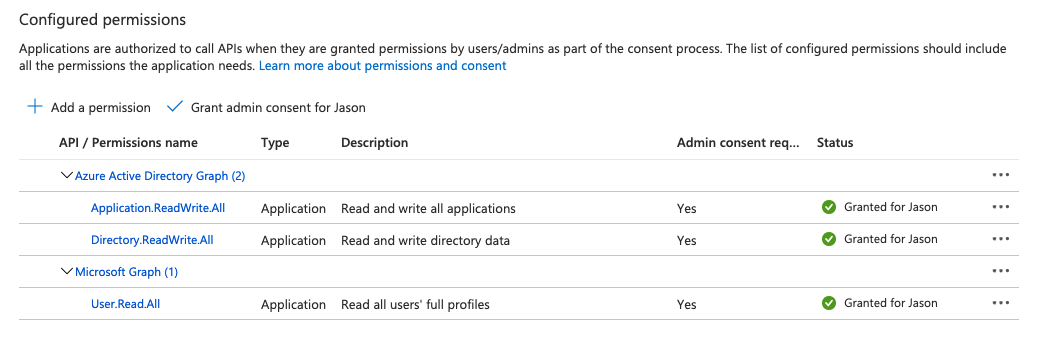
Build Hack And Defend Azure Identity Sans Institute
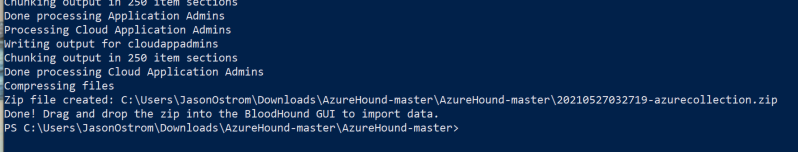
Build Hack And Defend Azure Identity Sans Institute
Github Dirkjanm Bloodhound Azuread Bloodhound With A Twist Of Cloud
Attacking Azure Azure Ad And Introducing Powerzure By Ryan Hausknecht Posts By Specterops Team Members
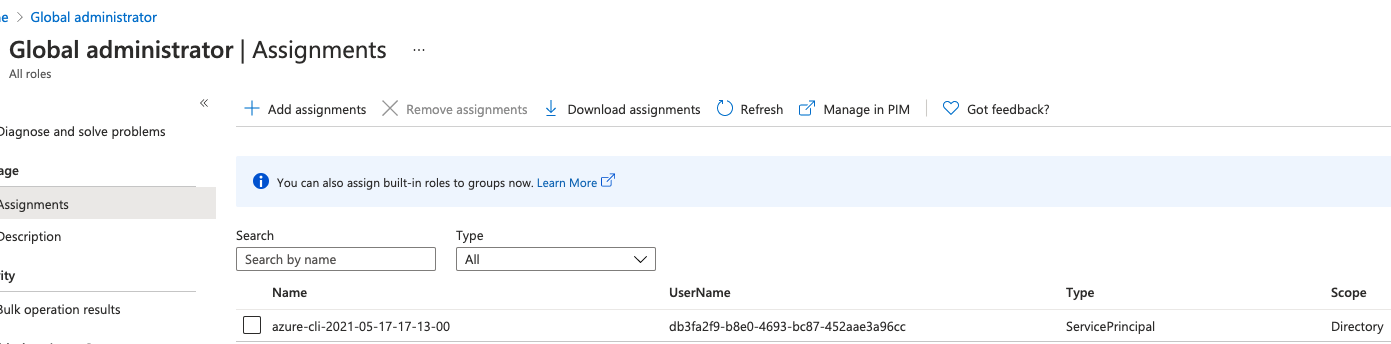
Build Hack And Defend Azure Identity Sans Institute

Pin On Attorney Logo Galleries
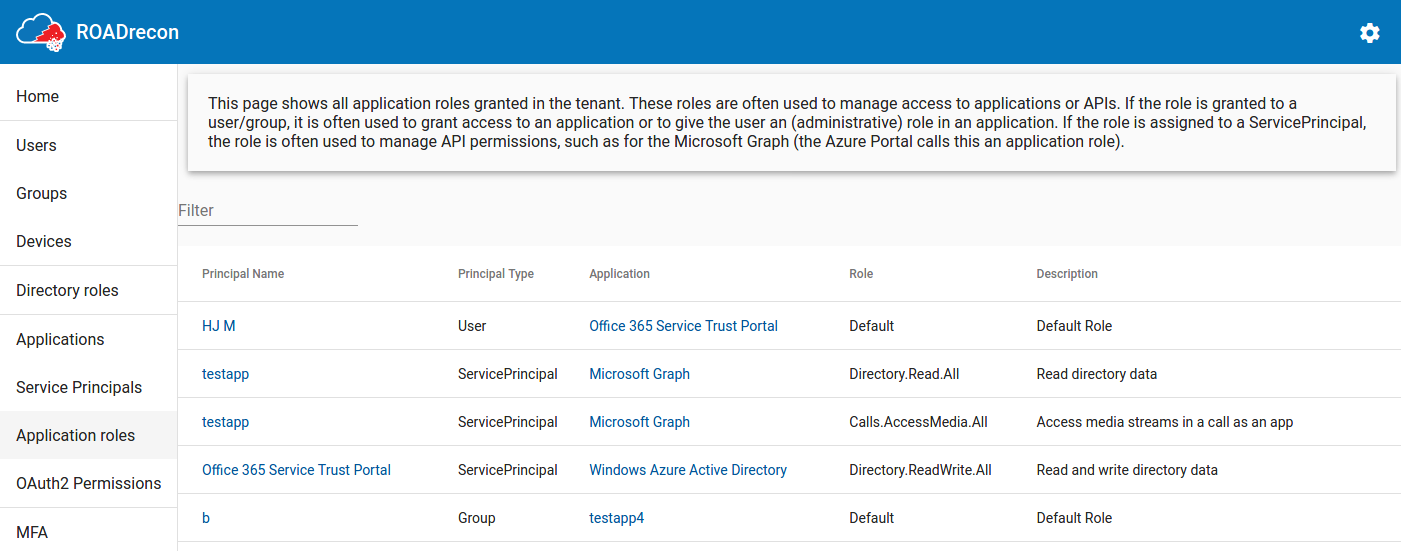
Introducing Roadtools The Azure Ad Exploration Framework Dirkjanm Io
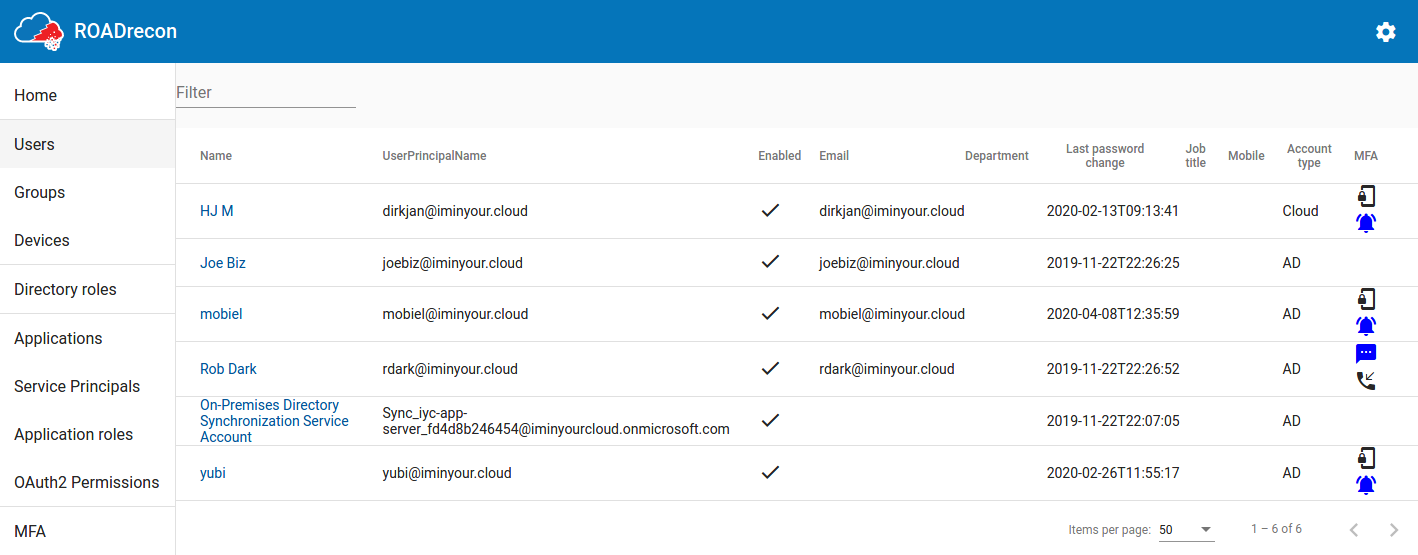
Introducing Roadtools The Azure Ad Exploration Framework Dirkjanm Io
Attacking Azure Azure Ad And Introducing Powerzure By Ryan Hausknecht Posts By Specterops Team Members

Github Evotecit Pswinreporting This Powershell Module Which Started As An Event Library Get Eventslibrary Ps1 Has Now G Event Id Active Directory Github

Attacking Active Directory Bloodhound Youtube
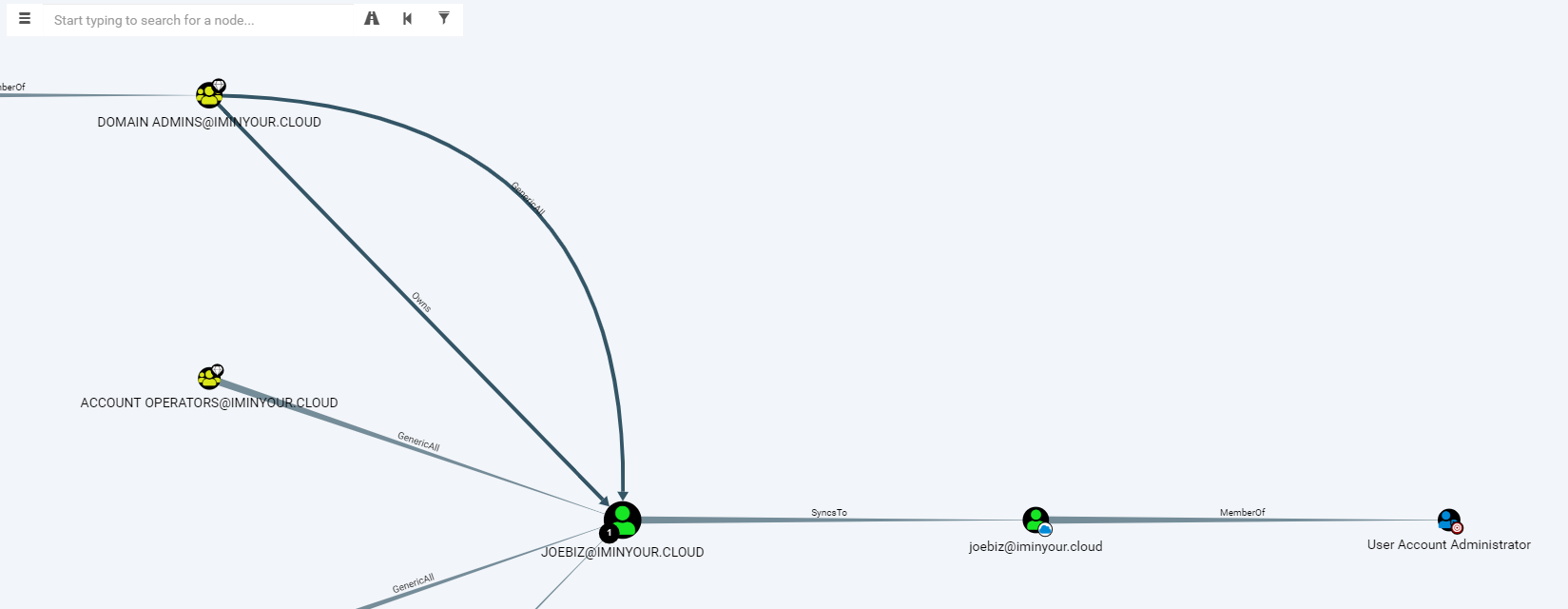
Introducing Roadtools The Azure Ad Exploration Framework Dirkjanm Io
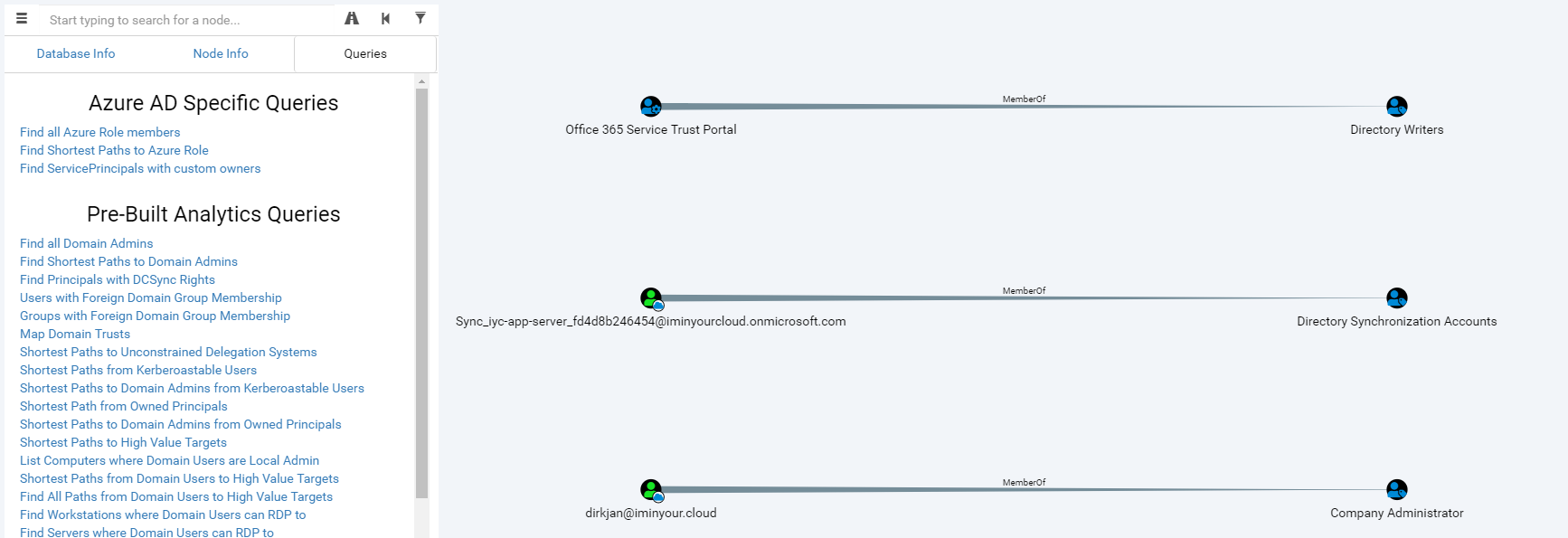
Introducing Roadtools The Azure Ad Exploration Framework Dirkjanm Io

Pin On News Office 365 Azure And Sharepoint

Pin On News Office 365 Azure And Sharepoint

Hunting For Reconnaissance Activities Using Ldap Search Filters
Build Hack And Defend Azure Identity Sans Institute